Atlassian is taking a significant step forward in ensuring the security of its cloud-based products. In this blog post, we’ll dive into Beacon, Atlassian’s latest innovation that promises to enhance the safety and security of your organization’s data and activities in the cloud.
Why Beacon Matters
Managing a multitude of cloud applications can be an overwhelming task, and failing to monitor them effectively can expose your business to significant risks. Beacon is here to change that. Think of it as Atlassian’s “system of intelligence” – an advanced engine designed to provide extended detection and response capabilities natively within Atlassian Cloud products.
What Does Beacon Do?
Beacon’s primary objective is to identify potential threats and security vulnerabilities in your Atlassian Cloud environment. It accomplishes this by spotting configurations that do not align with best security practices and by detecting anomalous user activity within your Atlassian Cloud products. With Beacon, you can rest assured that your cloud collaboration is secure across your entire organization.
Atlassian already prides itself on delivering world-class security and reliability, ensuring that your data remains safeguarded. Beacon takes it a step further by adding an additional layer of intelligence over your Atlassian Cloud products. It continuously monitors your environment and automatically alerts you when it detects suspicious or unusual user activities. These alerts cover a range of critical areas, including:
- Data Exfiltration:
- Exporting data such as Confluence page and space exports, Confluence site backups, Atlassian Access audit log exports, and identifying configuration changes.
- Unusual User Activity:
- User activity – these detections analyze user actions, and notify you about potentially risky behavior.
- Content scanning – these detections focus on data, and alert you when potentially sensitive data is added to Confluence pages.
- Unwanted Authorizations:
- Access and password changes such as admins logging in as another user (user impersonation), organization admin changes, and org admin password resets.
- Policy changes such as changes to IP allowlist policies, authentication policies, and adding or removing verified domains.
- Admin API key creation
- Marketplace App Changes:
- Marketplace app installation and removal: At the moment, these detections only fire for Forge apps, and when 3LO apps are installed for an org for the first time.
- Insecure Configurations:
- Public configuration: Application tunnel creation and removal, and anonymous or public access changes to Jira and Confluence.
- Organization admin changes
- Beacon user access
The Beacon Workflow
Now that we understand the critical role Beacon plays, let’s walk through how it works.
Alerts Dashboard: The first stop in your Beacon journey is the Alerts Dashboard. Here, you’ll find a list of alerts that represent potential security events identified by Beacon. Each of these alerts has the potential to impact your security posture.
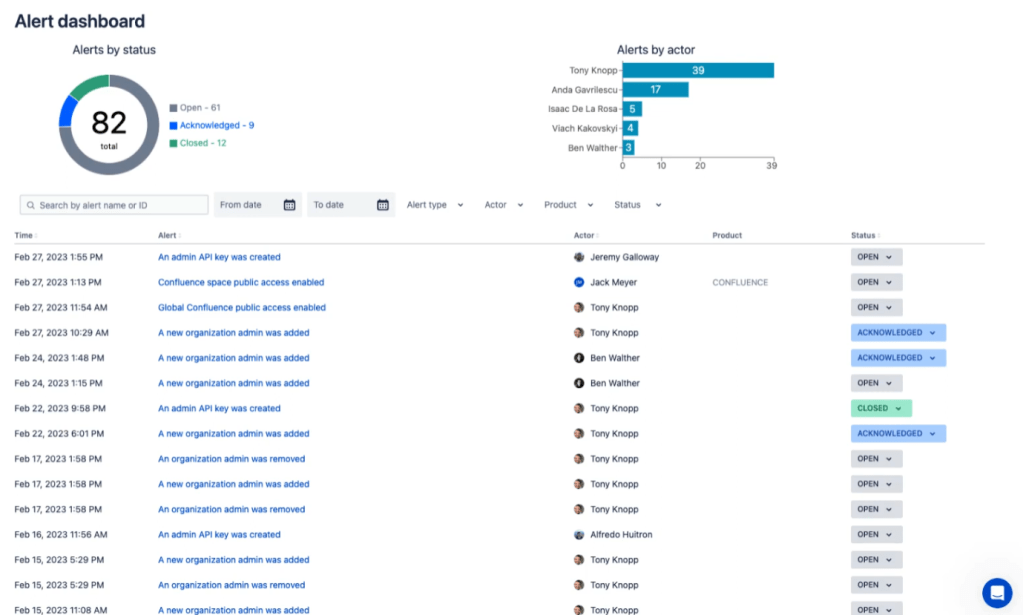
Investigate: You can click into individual alerts to investigate the details associated with them. This step is crucial in understanding the nature of the threat and its potential impact on your organization.
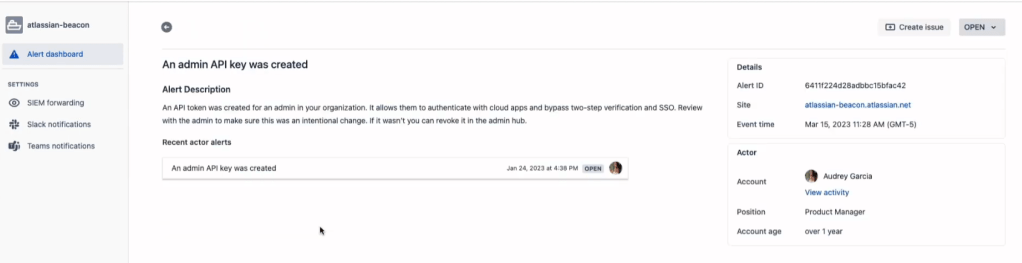
Response: Once you’ve investigated an alert, you can determine the right response for your team. Beacon provides a range of options to address the issue, from immediate action to escalation to other tools, such as Jira, to complete your workflow.
Integration and Customization: Beacon doesn’t stop at just alerting you within its platform. It can also seamlessly integrate with other security tools and systems, including Splunk, QRadar, and Sentinel. Additionally, it can forward alerts to popular chat apps like Slack and Teams, ensuring that alerts reach the teams that need to see them promptly.

It’s truly advantageous that Beacon offers integration with well-established SIEM solutions like Splunk. For large enterprises that have already implemented Security Information and Event Management (SIEM) tools, the ability to centralize alerts and incidents is of immense importance.
Complex Alerts: Beacon excels in handling complex alerts. For instance, it can detect unusual search activity in Confluence, alerting you when a user searches for sensitive terms in a short period. This kind of detection can be crucial in identifying potential data exfiltration attempts.
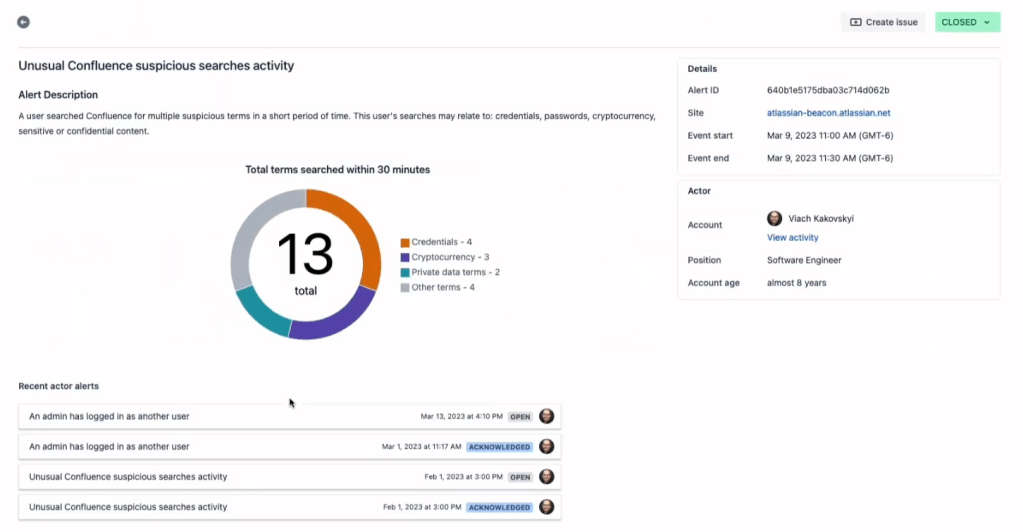
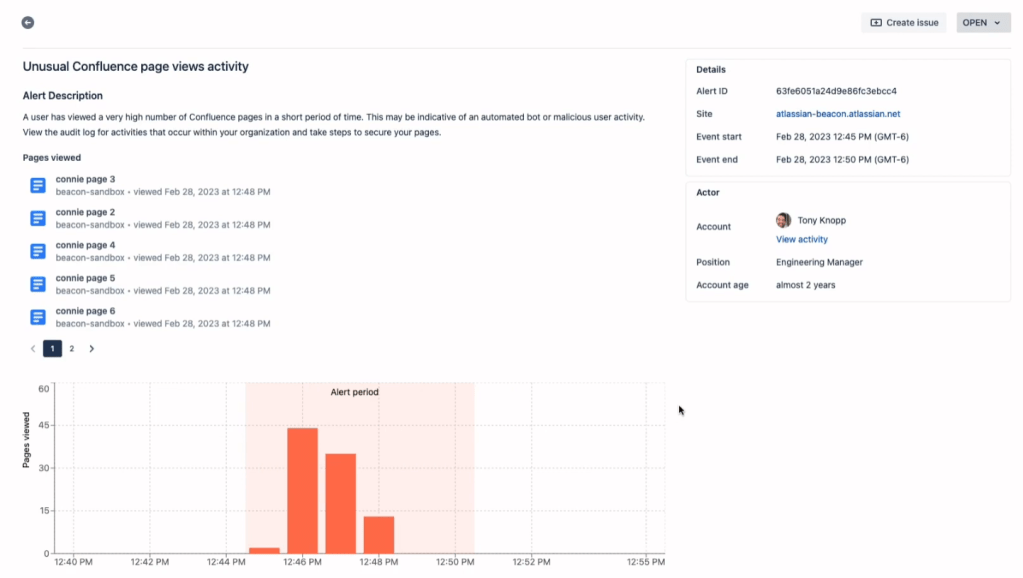
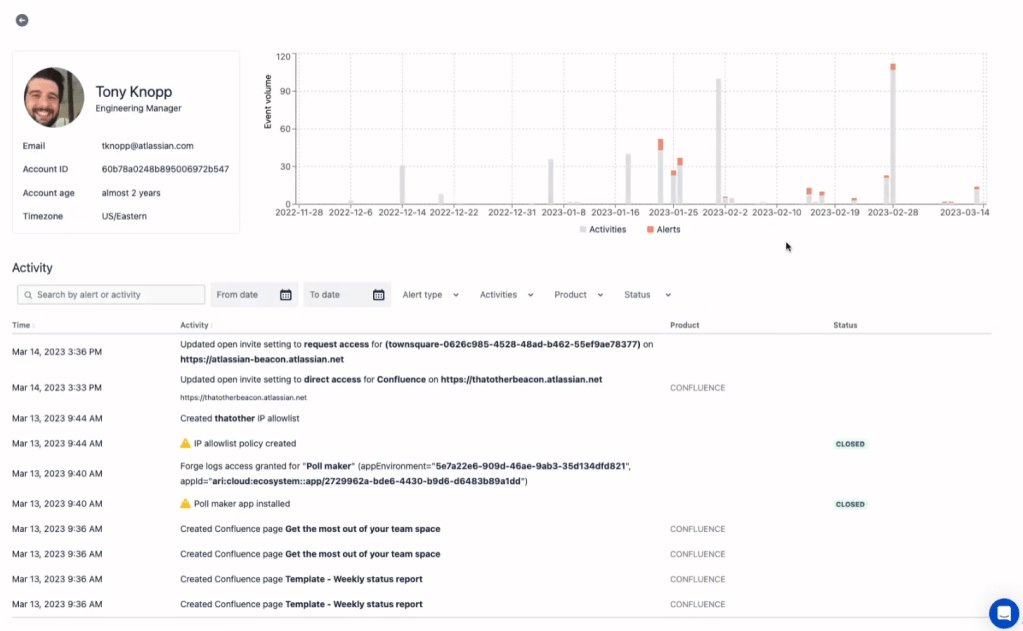
Investigation with Context: Beacon offers the tools you need to investigate alerts effectively. By providing context such as the user’s activity history, login locations, and other relevant information, Beacon helps you piece together the story behind each alert.
Conclusion
With Beacon by Atlassian, your organization gains a powerful ally in the ongoing battle against security threats in the cloud. It empowers you to detect, investigate, and respond to potential security incidents swiftly and effectively, providing peace of mind that your cloud collaboration remains secure.
Sources
